A new ransomware operation called RedAlert, or N13V, encrypts Windows and Linux VMWare ESXi servers during attacks on corporate networks.
The new operation was discovered today by MalwareHunterTeam, who tweeted various images from the gang’s data leak site.
The ransomware was called “RedAlert” based on a string used in the ransom note. However, from a Linux cipher obtained by BleepingComputer, hackers call their operation “N13V” internally, as shown below.
Source: BleepingComputer
The Linux encryptor is created to target VMware ESXi servers, with command-line options that allow hackers to shut down all running virtual machines before encrypting files.
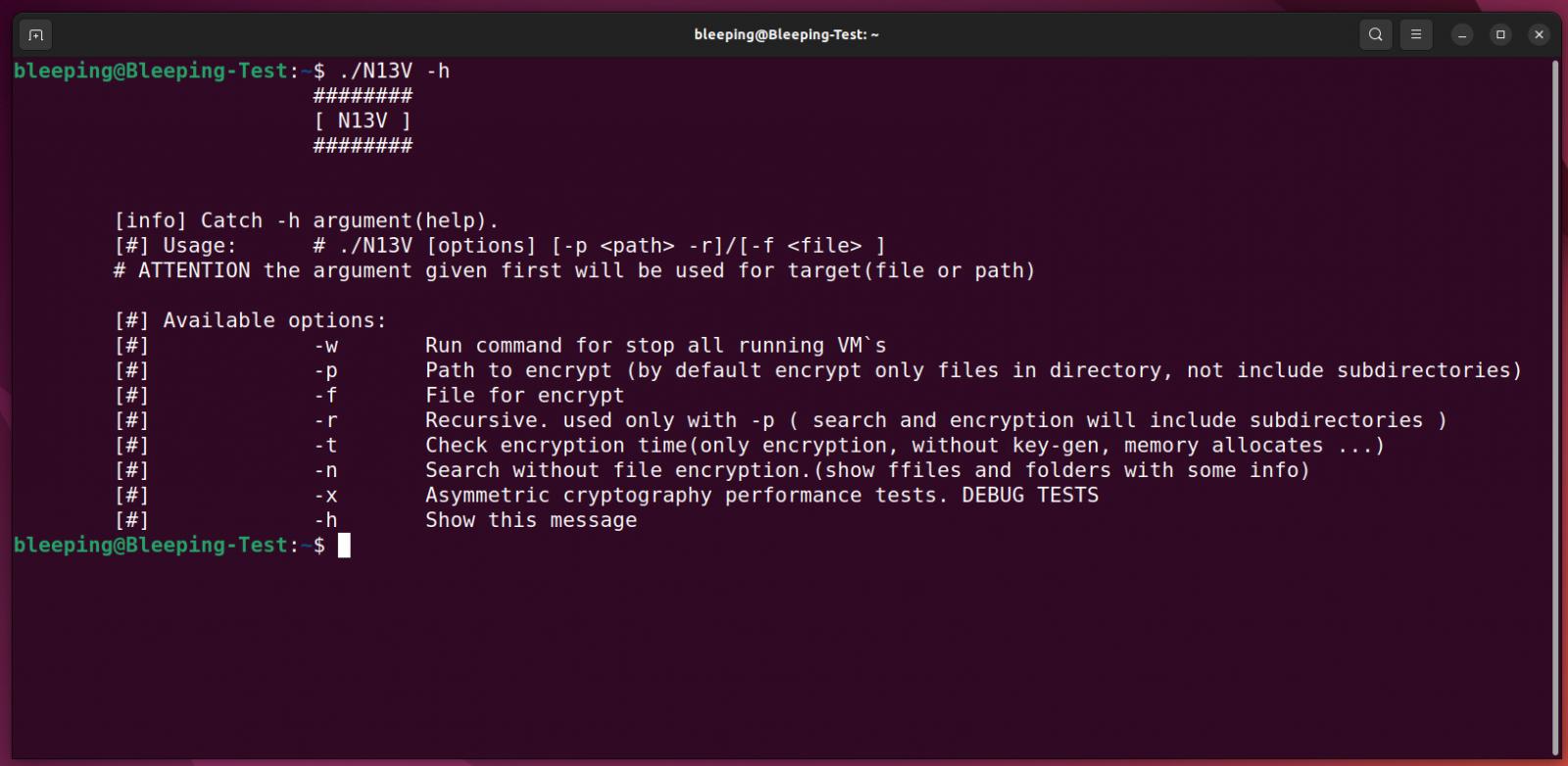
The full list of command line options can be viewed below.
-w Run command for stop all running VM`s
-p Path to encrypt (by default encrypt only files in directory, not include subdirectories)
-f File for encrypt
-r Recursive. used only with -p ( search and encryption will include subdirectories )
-t Check encryption time(only encryption, without key-gen, memory allocates ...)
-n Search without file encryption.(show ffiles and folders with some info)
-x Asymmetric cryptography performance tests. DEBUG TESTS
-h Show this messageWhen running the ransomware with the ‘-w‘, the Linux encryptor will shut down all running VMware ESXi virtual machines using the following esxcli command:
esxcli --formatter=csv --format-param=fields=="WorldID,DisplayName" vm process list | tail -n +2 | awk -F $',' '{system("esxcli vm process kill --type=force --world-id=" $1)}'
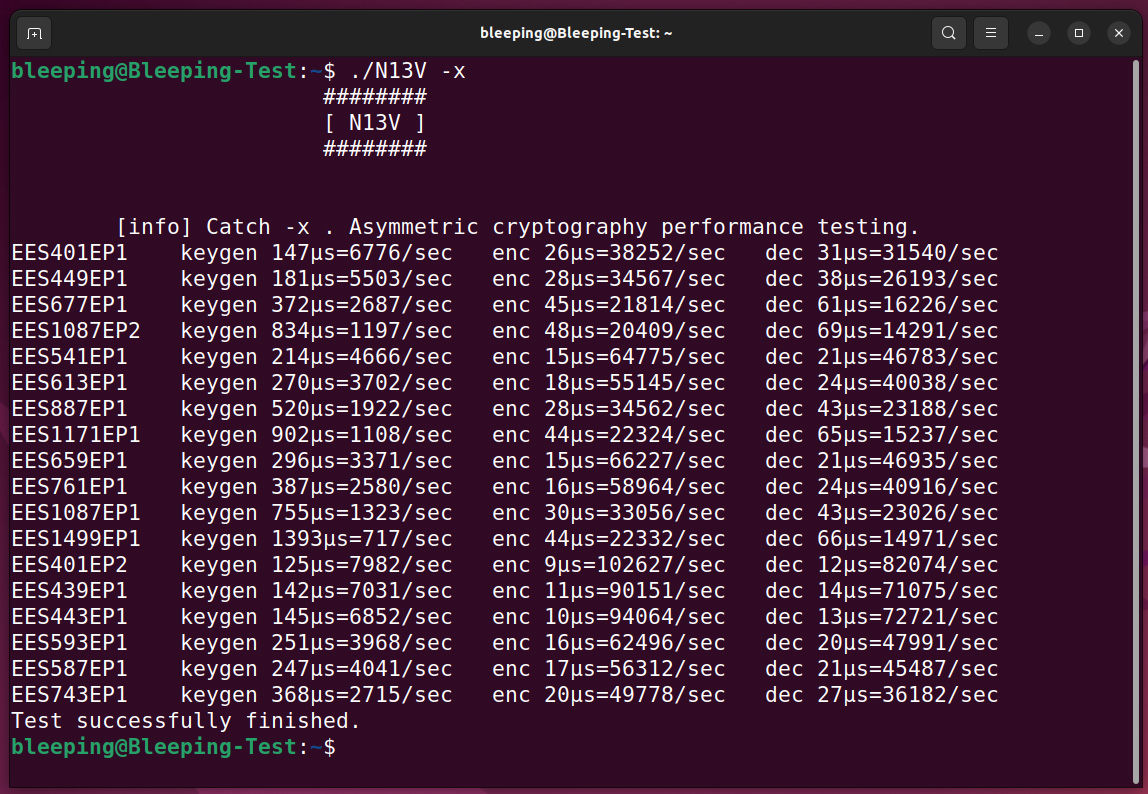
When encrypting files, the ransomware uses the NTRUEncrypt public-key encryption algorithm, which supports various “parameter sets” that provide different levels of security.
A nice feature of RedAlert/N13V is the ‘-x’ command line option which performs ‘asymmetric cryptography performance tests’ using these different sets of NTRUEncrypt parameters. However, it is unclear if there is a way to force a particular set of parameters when encrypting and/or if the ransomware will select a more efficient one.
The only other ransomware operation known to use this encryption algorithm is FiveHands.
Source: BleepingComputer
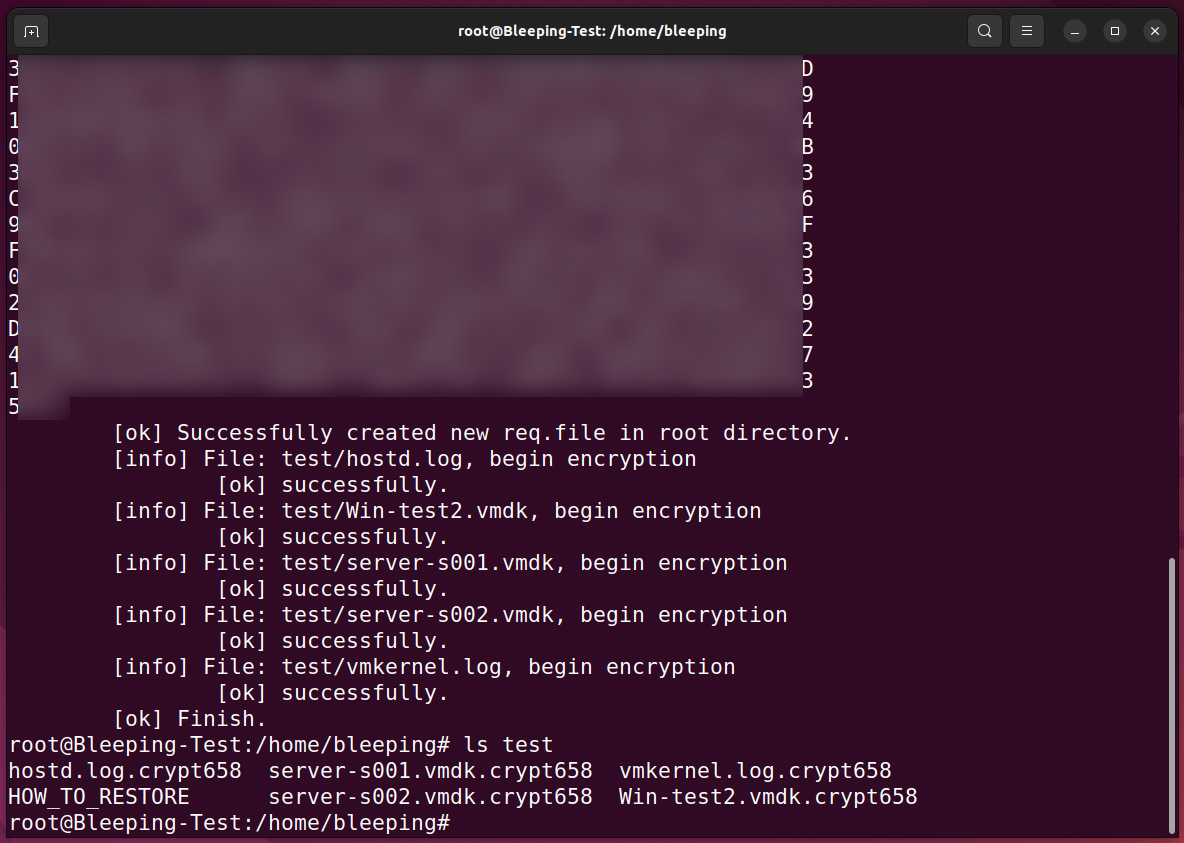
While encrypting files, the ransomware will only target files associated with VMware ESXi virtual machines, including log files, swap files, virtual disks, and memory files as shown below.
.log
.vmdk
.vmem
.vswp
.vmsnIn the sample analyzed by BleepingComputer, the ransomware would encrypt these file types and append the .crypt658 extension to filenames of encrypted files.
Source: BleepingComputer
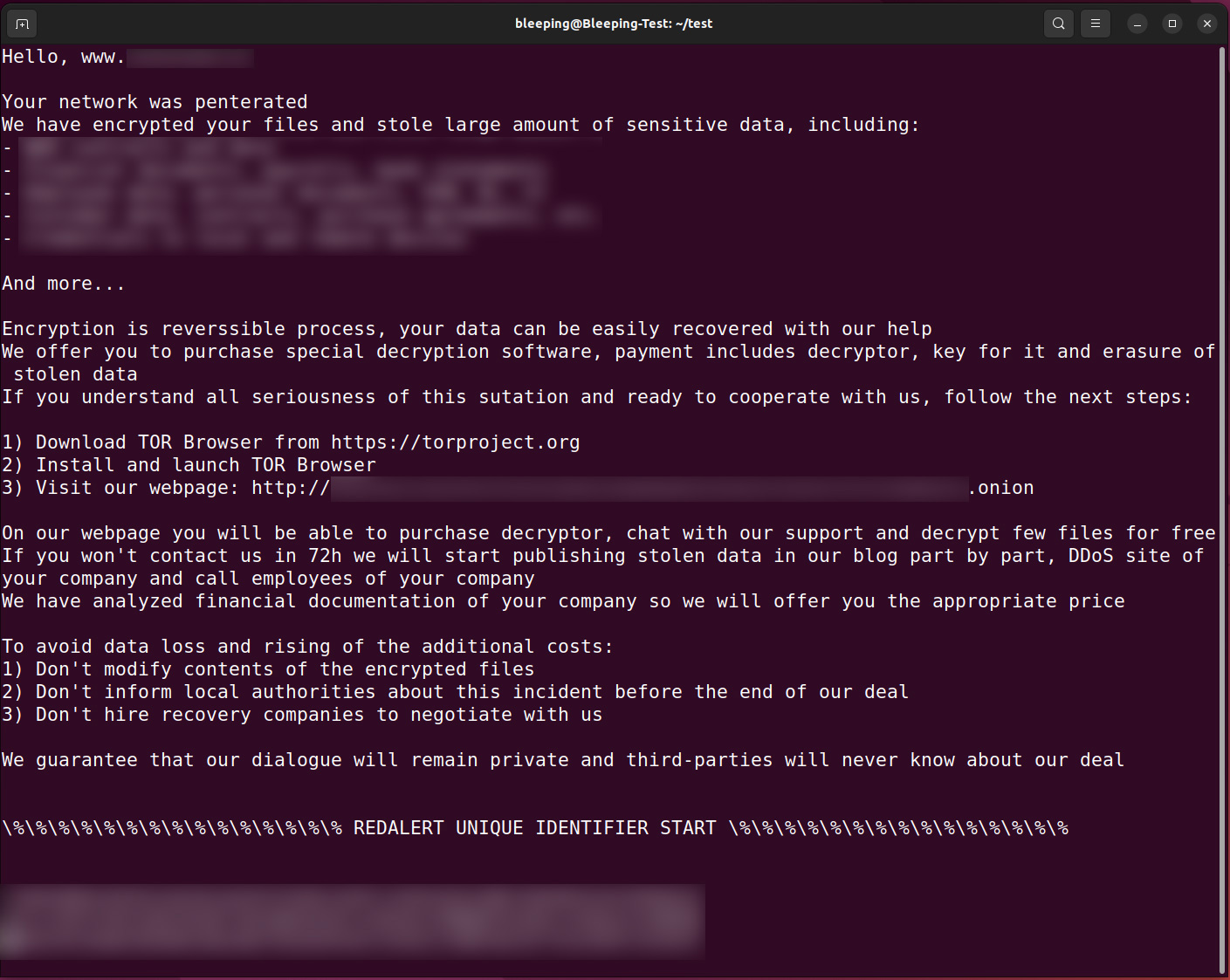
In each folder, the ransomware will also create a personalized ransom note named HOW_TO_RESTOREwhich contains a description of the stolen data and a link to a unique TOR ransom payment site for the victim.
Source: BleepingComputer
The Tor payment site is similar to other ransomware exploit sites in that it displays the ransom demand and offers a way to negotiate with threat actors.
However, RedAlert/N13V only accepts Monero cryptocurrency for payment, which is not commonly sold on crypto exchanges in the United States as it is a privacy coin.
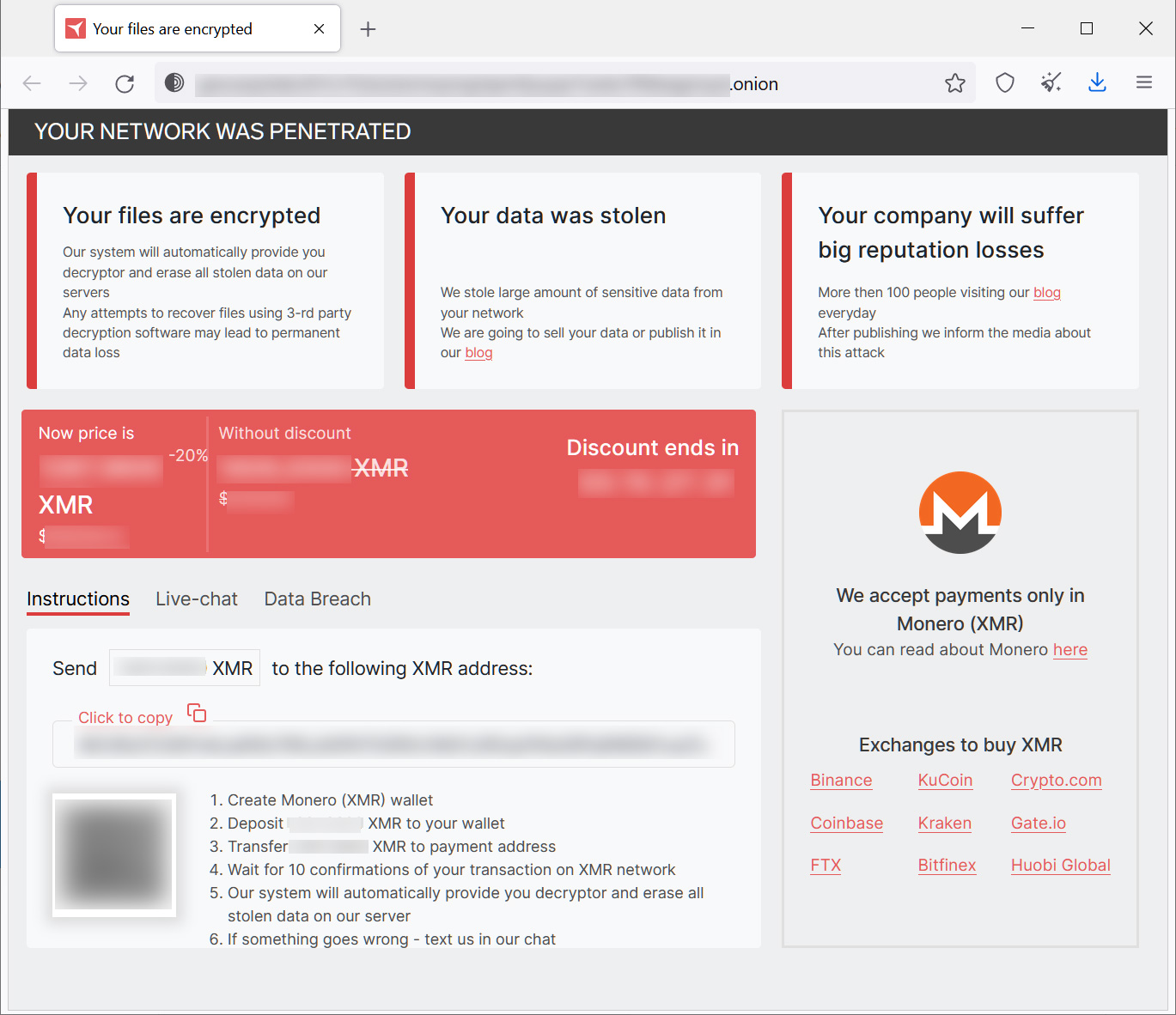
Source: BleepingComputer
While only a Linux encryptor was found, the payment site has hidden elements showing that Windows decryptors also exist.
“Council of Shame”
Like almost all new ransomware operations targeting businesses, RedAlert conducts double extortion attacks, which is where data is stolen and then ransomware is deployed to encrypt the devices.
This tactic provides two methods of extortion, allowing threat actors to not only demand a ransom to receive a decryptor, but also demand one to prevent the leak of stolen data.
When a victim fails to pay a ransom, the RedAlert gang posts stolen data on its data leak site for anyone to download.
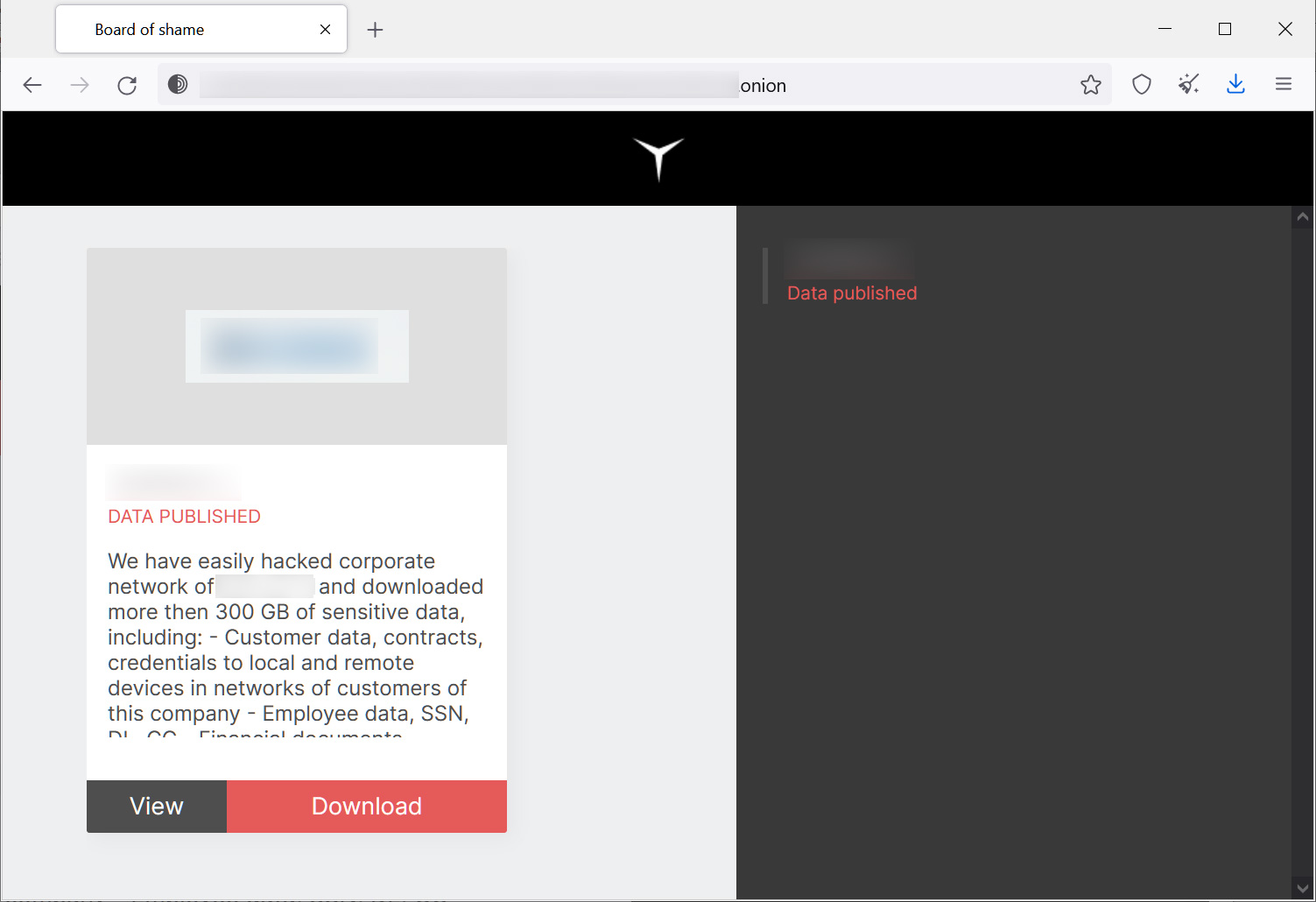
Source: BleepingComputer
Currently, the RedAlert data leak site only contains data from a single organization, indicating that the operation is very new.
While there hasn’t been much activity with the new N13V/RedAlert ransomware operation, it’s one we’ll definitely have to keep an eye on due to its advanced features and immediate support. for Linux and Windows.

